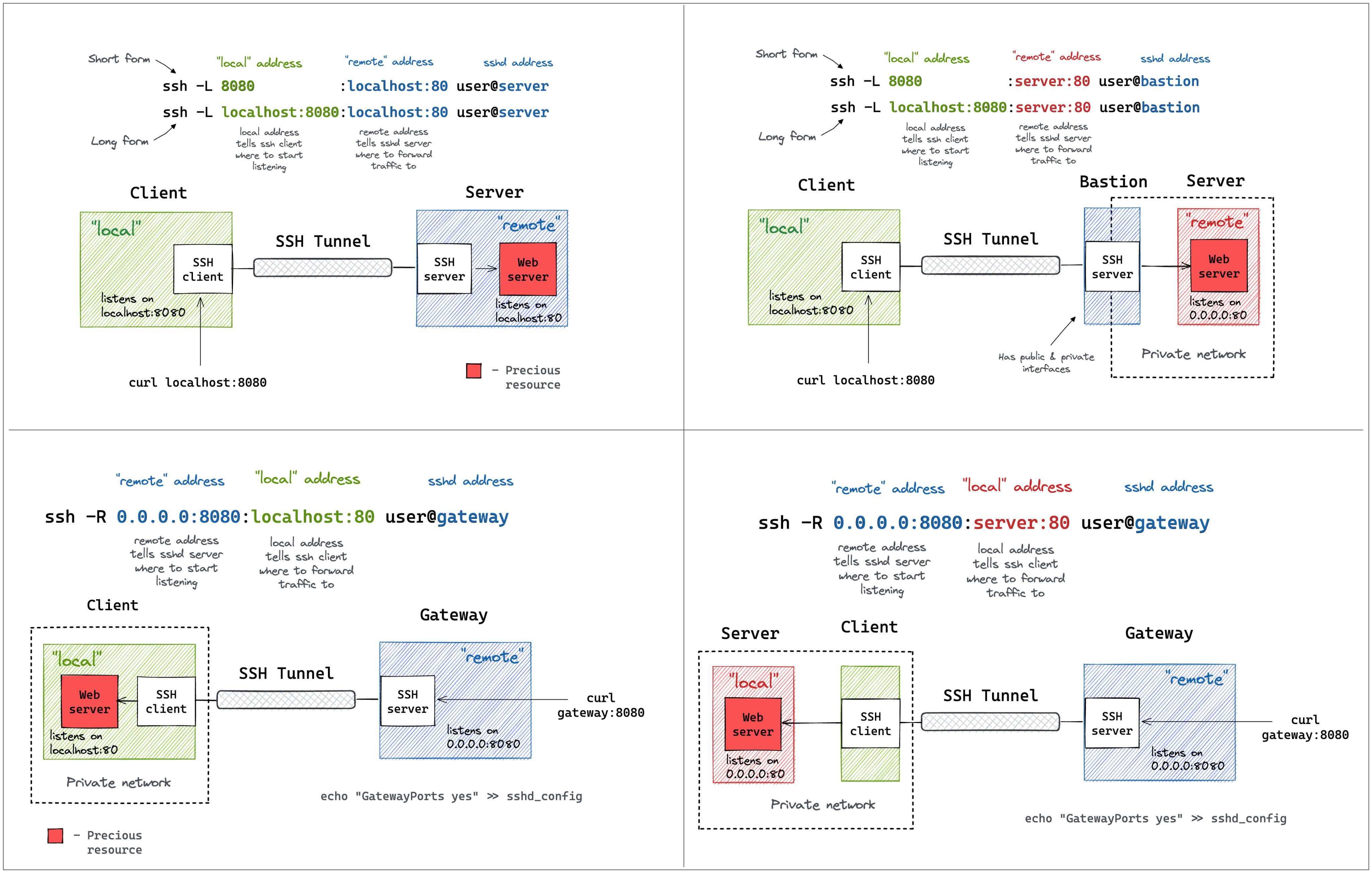
Local Port Forwarding (Top Left)
Usage:
Command: ssh -L 8080:localhost:80 user@server
This command sets up a local port forward where the SSH client listens on localhost:8080 and forwards any connections to localhost:80 on the remote server.
Benefits:
Accessing Internal Services: This is useful when you need to access a service running on a remote server that is not publicly accessible. For example, if you have a web server running on localhost:80 on the remote machine, you can access it through localhost:8080 on your local machine.
Security: Traffic is encrypted over the SSH tunnel, providing a secure way to access internal resources.
Local Port Forwarding with Bastion (Top Right)
Usage:
Command: ssh -L 8080:localhost:8080 user@bastion
This command is similar to the first but involves a bastion host (a jump server) which is often used in more secure environments where direct access to the target server isn’t allowed.
Benefits:
Enhanced Security: Adds an extra layer of security by requiring connection through a bastion host, which can be more tightly controlled.
Access Control: Useful in environments where direct SSH to internal servers is restricted, allowing access only through a controlled entry point.
Remote Port Forwarding (Bottom Left)
Usage:
Command: ssh -R 0.0.0.0:8080:localhost:80 user@gateway
Here, the SSH server (gateway) listens on 0.0.0.0:8080 and forwards traffic to localhost:80 on the client’s machine.
Benefits:
Exposing Local Services: This allows you to make a service running on your local machine available to others through the remote server. For instance, if you’re running a web server locally, you can make it accessible via the gateway server.
Reverse Proxy: Useful for scenarios where you need to expose internal services externally without direct exposure.
Remote Port Forwarding with Gateway (Bottom Right)
Usage:
Command: ssh -R 0.0.0.0:8080:server:80 user@gateway
Similar to the previous, but it forwards traffic from the gateway to another server (server:80) within the network.
Benefits:
Indirect Access: Allows for indirect access to services within a private network through a gateway, enhancing network security by not exposing internal IPs directly.
Load Balancing: Can be used in conjunction with load balancing strategies where traffic is directed through a gateway to distribute load across multiple internal servers.
General Benefits of SSH Tunneling:
Encryption: All data transferred through the tunnel is encrypted, providing a secure channel for communication.
Bypassing Firewalls: SSH tunneling can sometimes bypass firewalls or network restrictions that block direct access to certain ports or services.
Dynamic Port Forwarding: While not shown here, SSH can also be used for dynamic port forwarding (-D option), which acts as a SOCKS proxy, useful for more complex scenarios like web browsing through a secure tunnel.
Important Note: For all configurations involving GatewayPorts, setting GatewayPorts yes in the SSH server’s sshd_config file allows the SSH server to bind to all interfaces, which is necessary for remote port forwarding to work as intended.
Each of these configurations serves different scenarios in network security, access management, and service exposure, making SSH tunneling a versatile tool.