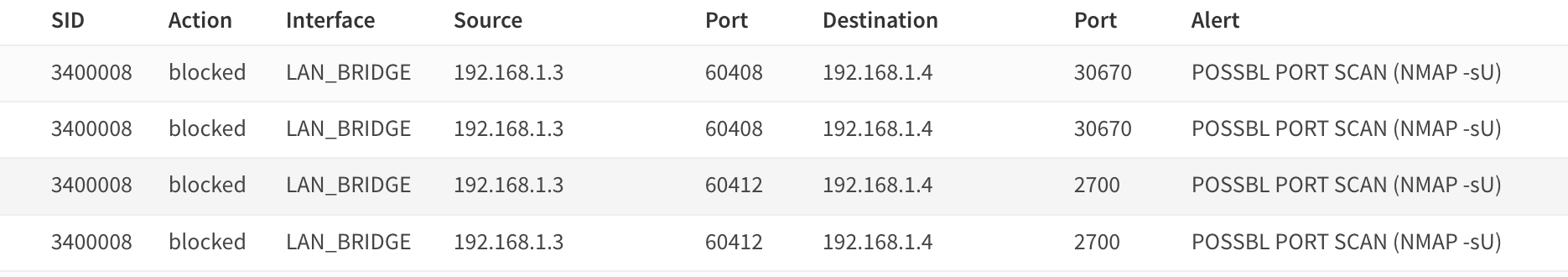
sudo nmap -sU -p 0-60000 x.x.x.x -T5
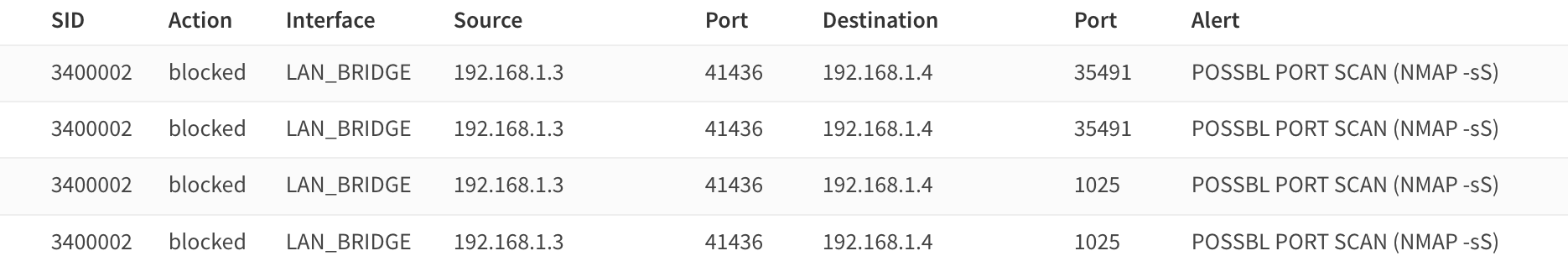
sudo nmap -sS -p 0-60000 x.x.x.x -T2
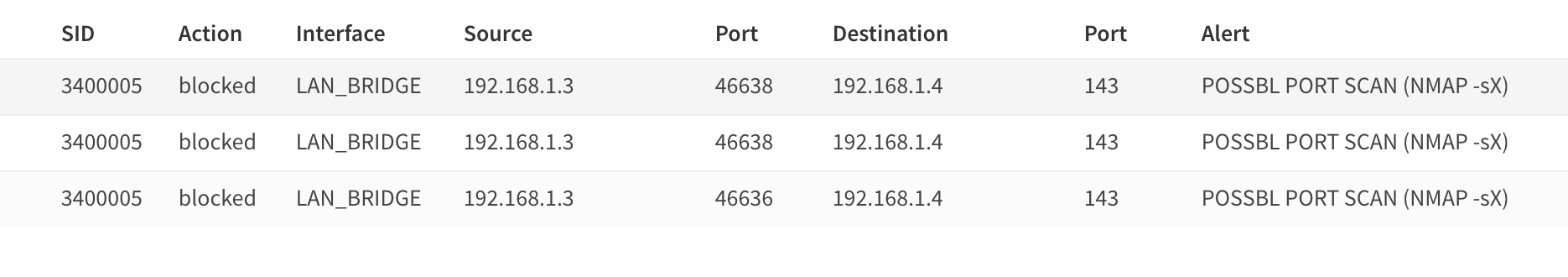
sudo nmap -sX -p 0-60000 x.x.x.x -T1
# For NMAP scan detection between scan speeds of T1-T5
# SYN SCAN -sS (speeds T1-T5)
alert tcp any any -> any [21,22,23,25,53,80,88,110,135,137,138,139,143,161,389,443,445,465,514,587,636,853,993,995,1194,1433,1720,3306,3389,8080,8443,11211,27017,51820] (msg:"POSSBL PORT SCAN (NMAP -sS)"; flow:to_server,stateless; flags:S; window:1024; tcp.mss:1460; threshold:type threshold, track by_src, count 20, seconds 70; classtype:attempted-recon; sid:3400001; priority:2; rev:1;)
alert tcp any any -> any ![21,22,23,25,53,80,88,110,135,137,138,139,143,161,389,443,445,465,514,587,636,853,993,995,1194,1433,1720,3306,3389,8080,8443,11211,27017,51820] (msg:"POSSBL PORT SCAN (NMAP -sS)"; flow:to_server,stateless; flags:S; window:1024; tcp.mss:1460; threshold:type threshold, track by_src, count 7, seconds 135; classtype:attempted-recon; sid:3400002; priority:2; rev:2;)
# SYN-ACK 3-WAY SCAN -sT (speeds T2-T5)
alert tcp any ![22,25,53,80,88,143,443,445,465,587,853,993,1194,8080,51820] -> any ![22,25,53,80,88,143,443,445,465,587,853,993,1194,8080,51820] (msg:"POSSBL PORT SCAN (NMAP -sT)"; flow:to_server; window:32120; flags:S; threshold:type threshold, track by_src, count 20, seconds 70; classtype:attempted-recon; sid:3400003; rev:3;)
# ACK SCAN -sA (speeds T2-T5)
alert tcp any ![22,25,53,80,88,143,443,445,465,587,853,993,1194,8080,51820] -> any ![22,25,53,80,88,143,443,445,465,587,853,993,1194,8080,51820] (msg:"POSSBL PORT SCAN (NMAP -sA)"; flags:A; flow:stateless; window:1024; threshold:type threshold, track by_dst, count 20, seconds 70; classtype:attempted-recon; sid:3400004; priority:2; rev:5;)
# CHRISTMAS TREE SCAN -sX (speeds T1-T5)
alert tcp any any -> any any (msg:"POSSBL PORT SCAN (NMAP -sX)"; flags:FPU; flow:to_server,stateless; threshold:type threshold, track by_src, count 3, seconds 120; classtype:attempted-recon; sid:3400005; rev:2;)
# FRAGMENTED SCAN -f (speeds T1-T5)
alert ip any any -> any any (msg:"POSSBL SCAN FRAG (NMAP -f)"; fragbits:M+D; threshold:type limit, track by_src, count 3, seconds 1210; classtype:attempted-recon; sid:3400006; priority:2; rev:6;)
# UDP SCAN -sU (speeds T1-T5)
alert udp any any -> any [53,67,68,69,123,161,162,389,520,1026,1027,1028,1029,1194,1434,1900,11211,12345,27017,51820] (msg:"POSSBL PORT SCAN (NMAP -sU)"; flow:to_server,stateless; classtype:attempted-recon; sid:3400007; priority:2; rev:6; threshold:type threshold, track by_src, count 20, seconds 70; dsize:0;)
alert udp any any -> any ![53,67,68,69,123,161,162,389,520,1026,1027,1028,1029,1194,1434,1900,11211,12345,27017,51820] (msg:"POSSBL PORT SCAN (NMAP -sU)"; flow:to_server,stateless; classtype:attempted-recon; sid:3400008; priority:2; rev:6; threshold:type threshold, track by_src, count 7, seconds 135; dsize:0;)
# For all usages of destination port 4444:
# TCP destination port: 4444
alert tcp any ![21,22,23,25,53,80,88,110,135,137,138,139,143,161,389,443,445,465,514,587,636,853,993,995,1194,1433,1720,3306,3389,8080,8443,11211,27017,51820] -> any 4444 (msg:"POSSBL SCAN SHELL M-SPLOIT TCP"; classtype:trojan-activity; sid:3400020; priority:1; rev:2;)
# UDP destination port: 4444
alert udp any ![53,67,68,69,123,161,162,389,520,1026,1027,1028,1029,1194,1434,1900,11211,12345,27017,51820] -> any 4444 (msg:"POSSBL SCAN SHELL M-SPLOIT UDP"; classtype:trojan-activity; sid:3400021; priority:1; rev:2;)
Suricata rules are stored in these two locations
Create a new file called namp.rules in the following two locations and paste the above rules. Restart Suricata after that with sudo service suricata restart
/usr/local/etc/suricata/opnsense.rules
/usr/local/etc/suricata/rules
Here is a detailed breakdown of each rule:
SYN SCAN (-sS)
Rule 1:
- Target Ports: Commonly scanned ports like 21 (FTP), 22 (SSH), 80 (HTTP), etc.
- Detection: Matches TCP packets with the SYN flag set (indicating the start of a connection).
- Threshold: Triggers an alert if 20 SYN packets from the same source are sent to these ports within 70 seconds.
- Flow: Stateless detection of packets to the server.
- Purpose: Detects high-speed SYN scans to common service ports.
Rule 2:
- Target Ports: All ports except the common ports listed above.
- Detection: Same as Rule 1, but triggers on uncommon ports.
- Threshold: Triggers if 7 SYN packets from the same source are sent to uncommon ports within 135 seconds.
- Purpose: Detects stealthier SYN scans targeting less common ports.
SYN-ACK 3-WAY SCAN (-sT)
- Rule 3:
- Target Ports: All except commonly used service ports (e.g., 22, 80, 443, etc.).
- Detection: Matches TCP packets with the SYN flag set.
- Threshold: Triggers if 20 packets are sent from the same source within 70 seconds.
- Purpose: Detects connection attempts from scans using the TCP three-way handshake (SYN, SYN-ACK, ACK).
ACK SCAN (-sA)
- Rule 4:
- Target Ports: All except commonly used service ports.
- Detection: Matches TCP packets with the ACK flag set.
- Threshold: Triggers if 20 ACK packets from the same source are sent to the destination within 70 seconds.
- Flow: Stateless detection.
- Purpose: Detects acknowledgment scans used to map out firewall rules or test for live hosts.
CHRISTMAS TREE SCAN (-sX)
- Rule 5:
- Target Ports: All.
- Detection: Matches TCP packets with FIN, PSH, and URG flags set (characteristic of Christmas tree scans).
- Threshold: Triggers if 3 such packets are sent from the same source within 120 seconds.
- Flow: Stateless detection.
- Purpose: Detects Christmas tree scans, typically used to analyze firewall configurations.
FRAGMENTED SCAN (-f)
- Rule 6:
- Target Ports: All.
- Detection: Matches fragmented packets with both “More Fragments” (M) and “Don’t Fragment” (D) flags set.
- Threshold: Triggers if 3 fragmented packets are sent from the same source within 1210 seconds.
- Purpose: Detects fragmented packets used to bypass intrusion detection systems (IDS).
UDP SCAN (-sU)
Rule 7:
- Target Ports: Commonly used UDP service ports like 53 (DNS), 67/68 (DHCP), 123 (NTP), etc.
- Detection: Matches UDP packets with no payload (dsize:0).
- Threshold: Triggers if 20 packets are sent from the same source within 70 seconds.
- Purpose: Detects fast UDP scans targeting common service ports.
Rule 8:
- Target Ports: All except commonly used UDP service ports.
- Detection: Same as Rule 7 but applies to less common ports.
- Threshold: Triggers if 7 packets are sent from the same source within 135 seconds.
- Purpose: Detects slower, more stealthy UDP scans on uncommon ports.
Shell Exploitation on Port 4444
TCP Destination Port 4444:
- Rule 9:
- Target: Any source sending TCP packets to port 4444.
- Purpose: Detects potential Metasploit (or other backdoor/trojan) activity often associated with port 4444.
- Rule 9:
UDP Destination Port 4444:
- Rule 10:
- Target: Any source sending UDP packets to port 4444.
- Purpose: Same as Rule 9 but applies to UDP packets, detecting possible Metasploit or other malicious activity.
- Rule 10:
